Author: mfeilner
#pineypoint is everywhere in the US…
‘No community should suffer this’: Florida’s toxic breach was decades in the making | Florida | The Guardian
https://www.theguardian.com/us-news/2021/apr/11/florida-piney-point-fertilizer-plant-toxic-leak
:-) #Clubhouse-Mitglieder Opfer eines #Hacker-Angriffs
#acatech #DigitaleSouveränität: Deutsche Akademie der Technikwissenschaften stellt Strategiepapiervor
Unter dem Titel “Digitale Souveränität – Status quo und Handlungsfelder” hat die Deutsche Akademie der Technikwissenschaften ein Strategiepapier zur Digitalen Souveränität vorgestellt. Die Autoren Henning Kagermann, Karl-Heinz Streibich und Katrin Suder beschreiben auf 36 Seiten, worauf es dabei in Deutschland und Europa besonders ankommt und entwickeln dazu ein Sieben-Ebenen-Schichtenmodell für Digitale Souveränität. Das reicht von der Abhängigkeit von Rohmaterialien bis hin zu einem Europäischen Werte- und Rechtssystem.
“Digitale Souveränität ist nicht nur eine Frage der Wettbewerbsfähigkeit, sondern auch der politischen Selbstbestimmtheit der Europäischen Union und ihrer Mitgliedsstaaten, der Innovationskraft von Unternehmen und der Freiheit der Forschungseinrichtungen und aller Europäer in der digitalen Welt.”
Unter den Interviewpartnern: OSB-Alliance-Vorstand Peter Ganten und SPRIND-Chef Rafael Laguna de la Vera.
Facebook faces US investigation for ‘systemic’ racial bias in hiring | Facebook | The Guardian
“A US agency investigating Facebook for racial bias in hiring and promotions has designated its inquiry as “systemic”, meaning it suspects company policies may be contributing to widespread discrimination”
Warum deutsche Schulen auf #MSTeams setzen? Weil es die Politik wollte. #homeschooling
Schulclouds am Kollaps: „Absichtlich gegen die Wand gefahren“ – Wissen – Tagesspiegel
Welcher Lehrer lässt sich noch auf ein Lernsystem ein, das tagelang nicht funktioniert, wenn er es unbedingt braucht?
(,,,)
Laut einem Zeitungsbericht wird die Schulcloud inzwischen von über 1000 Servern bereit gestellt. Bei IServ sind es noch mehr. Geschäftsführer Jörg Ludwig sagte dem Tagesspiegel: „Wir betreiben nur für unsere Videokonferenzen 1500 leistungsstarke Server, dazu kommen für IServ selbst 3000 lokale Server an den Schulen.“ Das sind die Größenverhältnisse: Mebis hat die meisten Schulen, aber die wenigsten Server. Die Konkurrenten stellen Hunderte bis Tausende zur Verfügung, Bayern ganze 36.
Und täglich grüßt der #Seehofer mit #verfassungsfeind lichen Aktionen. Kein Wunder, dass die radikalen mehr werden
Innovationsfeindlich und unausgereift: Das neue Telekommunikationsgesetz im Bundestag | mailbox.org
„Es kann nicht sein, dass der Gesetzgeber immer wieder versucht die Grenze des Erlaubten auszutesten und zu überschreiten, um dann vom Bundesverfassungsgericht auf den Boden der Tatsachen zurückgeholt zu werden. Das hat mit Rechtsstaatlichkeit nichts zu tun“, so Peer Heinlein, der mit mailbox.org derzeit selbst eine (bis heute unentschiedene) Verfassungsbeschwerde gegen die VDS beim Bundesverfassungsgericht in Karlsruhe eingereicht hat.
Datenverlust in Sachsen-Anhalt, Ost-Mafia hocherfreut…
“Wer in den letzten Wochen in Sachsen-Anhalt ein Verbrechen begangen hat, kommt möglicherweise straffrei davon, weil ihm die Tat nicht nachgewiesen werden kann.
In der Volksstimme spricht das LKA von einer “Fehlerkette”. Beim Bundeskriminalamt existiert eine Datensicherung. Jetzt wird hierüber probiert, die Daten wiederherzustellen.”
There’s still hope for the US: Meet the People’s Party of the US…
Movement For A People’s Party – A Party For Us
We need actual representation in our government. A majority of people in the US don’t feel represented by either the Democratic or Republican parties. We’ve watched these parties turn their backs on us to answer every call of the billionaires and donors.
Sacha Baron Cohen: ‘If you’re protesting against racism, you’re going to upset some racists’ | Film | The Guardian
“I’ve had threats since Ali G and in my experience publicising them only does one thing: lead to more threats. We are in a very violent time. If you’re protesting against racism, you’re going to upset some racists.”
https://www.theguardian.com/film/2021/feb/19/sacha-baron-cohen-borat-trial-chicago-7-facebook-trump
Die Lithiumkrise zeigt doch: Massenhafter Indivualverkehr ist tot
Wer in die Atacama-Wüste schaut, marktwirtschaftlich rechnet und sich die Strukturen mal unemotional anschaut, weiß dass weder Elektromobilität noch andere Verbrennungsmotoren wie H2-Verbrenner nicht die Zukunft sind. Die eignen sich gut, um das veraltete (Geschäfts)Modell des ubiquitären Individualverkehrs leisten können. Aber das hat leider keine Zukunft mehr, spätestens wenn man da auch das Verursacherprinzip anwendet. Marktwirtschaft halt, ganz sauber und eiskalt kalkuliert, volkswirtschaftlich.
Hosting #OwnCloud #OCIS on #Ubernauten
 Uberspace is one of the lesser known free hosters around. With the claim “Hosting on Steroids” they offer free-of-charge hosting for everybody – for a month. They have extremely extensive documentation in their wiki, but Owncloud oCIS wasn’t documented there. And since tools like that require some configuration specific to uberspace, here’s a little howto get it started.
Uberspace is one of the lesser known free hosters around. With the claim “Hosting on Steroids” they offer free-of-charge hosting for everybody – for a month. They have extremely extensive documentation in their wiki, but Owncloud oCIS wasn’t documented there. And since tools like that require some configuration specific to uberspace, here’s a little howto get it started.
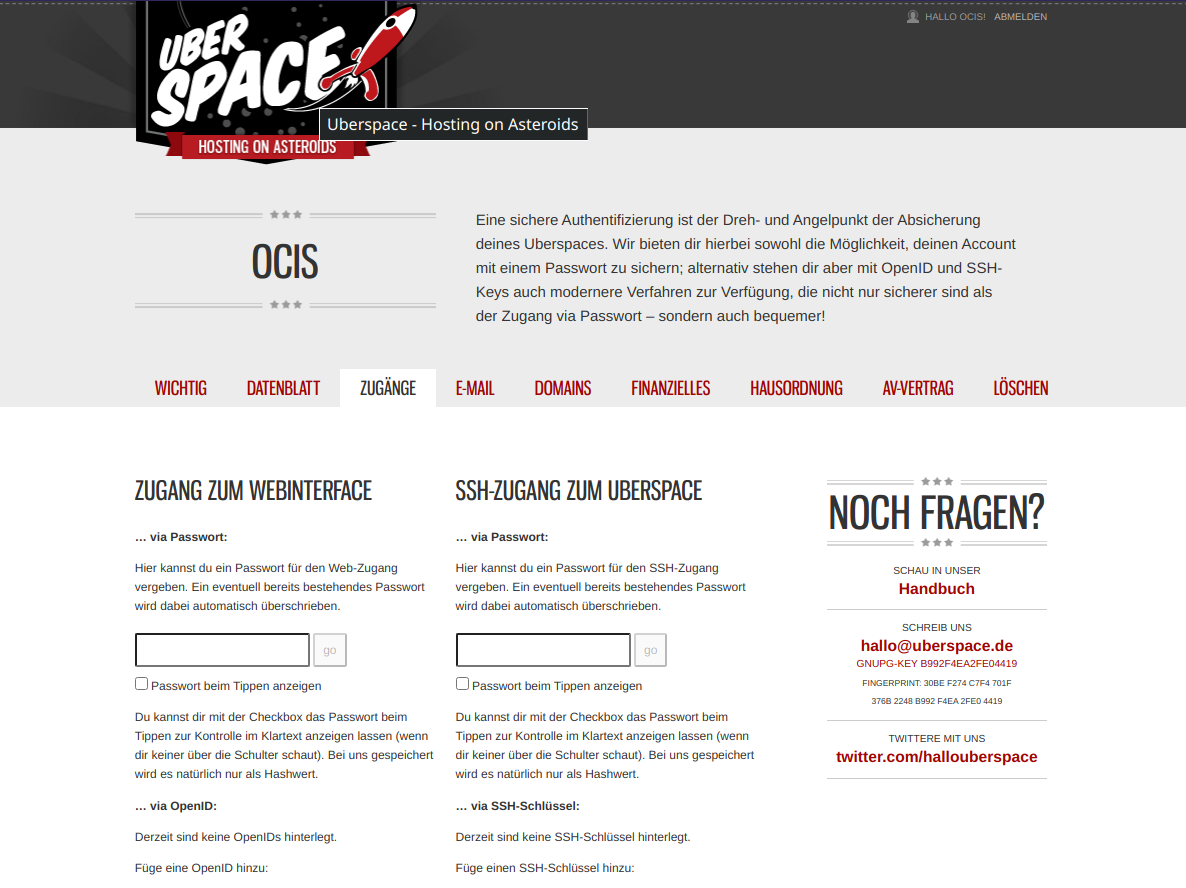
Go to the “Ubernauten” website and register. The first month is for free, the 5 Euro product is enough for testing and running your first oCIS setup. I enter my e-mail-address, my favorite subdomain name (ocis for this blogpost) and confirmed. That’s it, ready to go. Please note the fqdn name of the server the Ubernauten give you, in my case it is hamal.uberspace.de.
You can now try to login via SSH, but that will fail because you haven’t set a password or a SSH-Key.:
ssh ocis@hamal.uberspace.de
The authenticity of host ‘hamal.uberspace.de (95.143.172.250)’ can’t be established.
ED25519 key fingerprint is SHA256:LGidXSzKaOcgBJWPtGEd049A5CDXIUIeqTz3IU/tU2I.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added ‘hamal.uberspace.de,95.143.172.250’ (ED25519) to the list of known hosts.
Password:
Password and SSH Key can be entered here (also linked from your datasheet). As you can see in the screen shot, OpenID is also an option. For security, you should use either SSH-Key or Open ID, not the password option. Upload your key, and login again:
# ~/.ssh> ssh ocis@hamal.uberspace.de
Last failed login: Sun Feb 7 19:30:15 CET 2021 from 37.4.224.245 on ssh:notty
There was 1 failed login attempt since the last successful login.
Last login: Sun Feb 7 19:15:09 2021
Welcome to Uberspace 7!
Current version: 7.9.0.0
Manual: https://manual.uberspace.de/en/
Watch out for changes at: https://manual.uberspace.de/en/changelog.html
Follow us on Twitter for updates: https://twitter.com/ubernauten
Is something unclear or does not work as expected?
=> check the server status: https://is.uberspace.online
=> reach out to our team: hallo@uberspace.de
[ocis@hamal ~]$
Now it’s time to download ocis (via curl) from the ownCloud download mirror:
[ocis@hamal ~]$ curl https://download.owncloud.com/ocis/ocis/stable/2.0.0/ocis-2.0.0-linux-amd64
–output ocis
(…)
[ocis@hamal ~]$ chmod +x ocis
[ocis@hamal ~]$
 Okay, time to start oCIS with ./ocis server, says Owncloud’s manual. But not on Uberspace – where we find some “special” conditions:
Okay, time to start oCIS with ./ocis server, says Owncloud’s manual. But not on Uberspace – where we find some “special” conditions:
- You don’t have root access
- A firewall blocks all ports other than 80,21,22,443 and maybe some more that webdevs need
- oCIS needs port 9200 to be accessible.
NginX to the rescue! Uberspace provides a proxy server that may reroute incoming requests to your local port 9200 – which is where oCIS is listening. So unless we have configured this proxy, the blank Ubernauten default html screen will be visible on ocis.uber.space. Thank God it’s all well documented in the Uberspace Manual, so here’s the steps needed for that:
uberspace web backend set / –http –port 9200
… which configures nginX to forward all requests to port 9200 of the local machine. The command
uberspace web backend list
/ http:9200 => NOT OK, no service
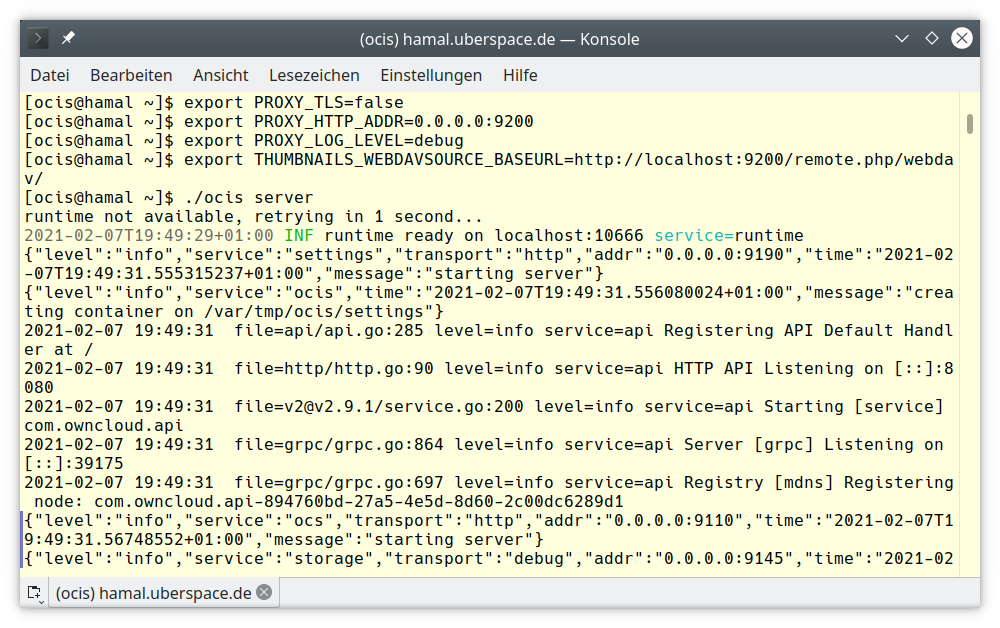 lets you check the success of the command before. Since there’s no local service running to answer, it’s NOT OK, but configuring the port 9200 to be redirected to our little ubenauten server has worked. Before we set up oCIS, we need some environment variables to be set aka exported:
lets you check the success of the command before. Since there’s no local service running to answer, it’s NOT OK, but configuring the port 9200 to be redirected to our little ubenauten server has worked. Before we set up oCIS, we need some environment variables to be set aka exported:
[ocis@hamal ~]$ export OCIS_URL=https://ocis.uber.space
[ocis@hamal ~]$ export PROXY_TLS=false
[ocis@hamal ~]$ export PROXY_HTTP_ADDR=0.0.0.0:9200
[ocis@hamal ~]$ export PROXY_LOG_LEVEL=debug
[ocis@hamal ~]$ export THUMBNAILS_WEBDAVSOURCEBASE_URL=http://localhost:9200/remote.php/webdav/
[ocis@hamal ~]$ ./ocis server
With these lines you have told oCIS to listen to the desired URL, communicate through HTTP with the proxy and which adress to listen on. We set the log level to debug, be sure to unset that once your system is up and running. The last export is a variable that the current oCIS version needed in order to display previews for image files correctly (thumbnails). The command in the last line finally starts oCIS, you will see the following login window:
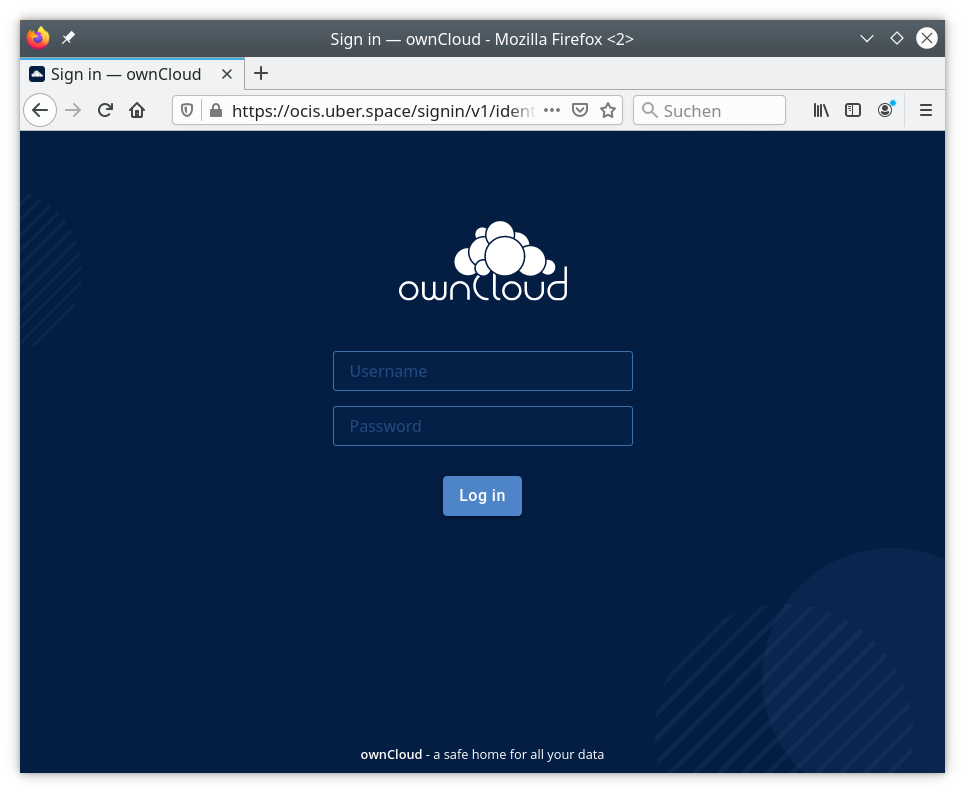
If you want to login, use the default users as mentioned on the owncloud documentation: Usage
Login to ownCloud Web
Open https://localhost:9200 and login using one of the demo accounts:
einstein:relativity
marie:radioactivity
richard:superfluidity
There are admin demo accounts:
moss:vista
admin:admin
As a test, you can now drag and drop files into oCIS. That’s it.
During the next days, I will try to get this article into the official Uberspace documentation on github, but that is hard, because it takes quite some time to follow their requirements, and there’s a lengthy style guide for contributors that does not make sense to learn for one-time-committers. It’s fine though for internal work of an editorial team, I guess.
(Housekeeping) #Backup Script for #Nextcloud
I don’t know if others need that too, but it seems just naturally to post this tiny little piece of bash which is our Nextcloud backup script. And I am perfectly aware that this is SME style, not big iron. 🙂 And if you don’t like Databases or PHP, have a look at Owncloud Infinite Scale.
These two products have been targeting more and more diverging directions since their fork: Owncloud adresses large scale, scalable datacenter customers (like CERN) and promises 10 times faster speed than their own PHP solution, but Nextcloud is carving out market share from MS365 customers with gazillions of apps in their app store and a large PHP community – with all benefits and downsides. Raise your hand if you never had to deactivate some community app to make an update work! 🙂
MySQL-Root-Password
Important: your MariaDB-Passwort will be in this file, I didn’t spend much time into investigating workarounds, but a chmod 700 of this file (read-write-execute) for root only seems appropriate. The DB is not listening on anything else but localhost, thus I am ready to accept this. If there’s a simple solution I missed, answer on Twitter or drop me a PM/Mail/Matrix message.
The Backup Script
As you can see I am backing up to a separate volume. I have file servers in several locations that fetch their backups (the tar files) from there. I don’t want the root fs run full, thus I don’t do a backup if /backup is not mounted. Alerting is done elsewhere. 🙂 On other systems, I mount the backup drive during such a script’s run. If you’re (like me) a seasoned but unexperienced Bash starter, add some “sleep 30” between the lines to see what’s happening and to easily break the script’s run. And you may or may not want the option –delete for rsync – your mileage may vary – and sorry for wordpress changing dashes and hyphens (Remember “Non-hyphenated is an example of a hyphenated word”).
#!/bin/bash
# Backing up Nextcloud Server
# Database Root password is in here, so chmod 700 this file!
DIR=/var/www/nextcloud #Source
BACKUPDIR=/backup/nextcloud #Target
BACKUPTAR=/backup/current_nextcloud_backup.tar.gz
DBPASS=YOUR_PASSWORD_HERE
if grep -qs ‘/backup ‘ /proc/mounts; then
echo“Backup disk is mounted. Proceeding with backup from $DIR/.“
echo“Entering nextcloud directory“
cd /var/www/nextcloud
echo“Putting NC into maintenance mode“
sudo -u www-data php occ maintenance:mode –on
echo“Backing up folders and config with Rsync:“
# sleep 30
/usr/bin/nice -18 /usr/bin/rsync -Aavz –delete $DIR/ $BACKUPDIR/
echo“Backing up MySQL data base ‘nextcloud’ :“
mysqldump –single-transaction -h localhost -u root -p$DBPASS nextcloud > $BACKUPDIR/nextcloud-sqlbkp_`date +“%Y%m%d“`.bak
sudo -u www-data php occ maintenance:mode –off
/usr/bin/nice -18 /bin/tar -czf $BACKUPTAR $BACKUPDIR
else
echo“Sorry, Backup disk is not mounted, quitting. CU again tomorrow.“
fi
Update:
I have two aliases on my NC servers:
alias ncd=’cd /var/www/nextcloud’
alias occf=’sudo -u www-data php ./occ’
With these I don’t need to bother about different document root directories (Debian/Ubuntu/Suse) nor remember the sudo… syntax (yes, I’m old) :-).
That proves helpful to do a lot of occ commands, like cleaning up the hard way:
occf trashbin:cleanup –all-users
occf versions:cleanup –all-users
clean up all trashbins and remove all old versions of files (yes ALL!).
If you don’t want Nextcloud to slowly fill up your hard drive / storage, add this to the config.php file:
‘trashbin_retention_obligation’ => ‘auto’,
‘versions_retention_obligation’ => 60, ‘auto’,
These two options will make Nextcloud store only files that are younger than 30 in the trashbin and versions of files no longer than 60 days.
#openSUSE in #RaspberryPi – Quickstart Guide
#Leaflet … notice to self… study.
Leaflet – a JavaScript library for interactive maps
Leaflet is the leading open-source JavaScript library for mobile-friendly interactive maps. Weighing just about 39 KB of JS, it has all the mapping features most developers ever need. Leaflet is designed with simplicity, performance and usability in mind. It works efficiently across all major desktop and mobile platforms, can be extended with lots of plugins, has a beautiful, easy to use and well-documented API and a simple, readable source code that is a joy to contribute to.
#Microsoft Repo Default on #RaspberryPi?
Microsoft repo secretly installed on all Raspberry Pi’s Linux OS – nixCraft
“In a recent update, the Raspberry Pi OS installed a Microsoft apt repository on all machines running Raspberry Pi OS without the person’s or admin’s knowledge. Every time a Raspbian device is updated by having this repo, it will ping a Microsoft server. Microsoft telemetry has a bad reputation in the Linux community. Let us see why and how this matters to Linux users.”
Dislaimer: Haven’t checked this yet, I can hardly imagine…
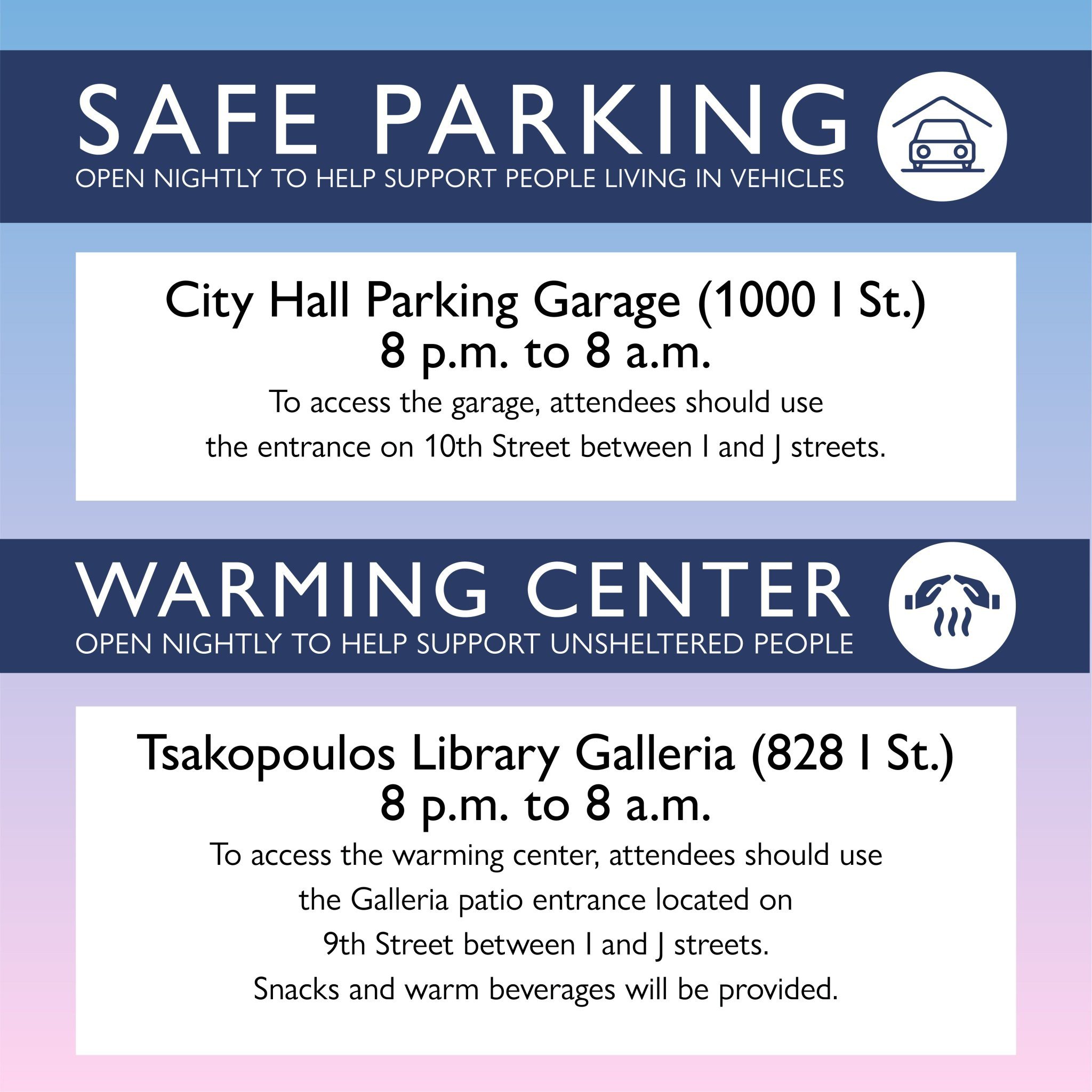
Only Americans will understand this correctly at first glance.
This is help for homeless people in Sacramento, CA, who are living in a car and have a job during daytime. During the current cold snow weather. There’s so many of them that the authorities had to prepare a shelter… Mind the colors.
#emobility : Inexpensive battery charges rapidly for electric vehicles, reduces range anxiety | Penn State University
PGP/S-MIME on Linux Command Line, helping Kontact (and other Mailers)
I recently had to decrypt a PGP/S-MIME encrypted mail. It’s been a long time since I was confronted with that format, and KDE’s Kontact does not seem to support this out of the box– actually only Thunderbird seems to do, and that’s not on my machines. Here’s what I did.
This Mail came in.
With the right PGP-Key I could decrypt it:
Upsii… there’s another encrypted file in there, exactly as the standard RFC from 2001 defines – this way even attachments are hidden from those that don’t have the private PGP key.
Since KDE’s crypto engine couldn’t help, and Thunderbird is not configured on my machines, I went to the command line. I saved the attachment “encrypted.asc” and ran the command “gpg –output uncrypted.asc –decrypt encrypted.asc“:
mfeilner@alquarismi:~/Downloads> gpg –output uncrypted.asc –decrypt encrypted.asc
gpg: WARNUNG: Unsichere Zugriffsrechte des Home-Verzeichnis `/home/mfeilner/.gnupg’
gpg: verschlüsselt mit 4096-Bit RSA Schlüssel, ID XXXXXXXXXXXXXXXXX, erzeugt 2015-04-24
(…)
gpg: verschlüsselt mit 2048-Bit RSA Schlüssel, ID XXXXXXXXXXXXXXXXX, erzeugt 2018-12-25
(…)
mfeilner@alquarismi:~/Downloads>
… and that way I got a file named uncrypted.asc that I could open with my favorite text editor or emacs.