“ls -l `find /feilner-it-backup/ -type f -printf “%T@ %p\n” | sort -n | cut -d’ ‘ -f 2- | tail -n 1`”
Mind that there’s three different kinds of upticks/quotation marks in this command… And yes,I am sure there’s a find parameter or an xargs command to do the same as the command substitution for ls – but that’s what worked for me, without research. I am not an expert, remember.
Category: Linux and OSS hints
April fools fun – set volume to battery level
This will set your Linux system’s volume to the battery level of a remote smartphone somewhere in your Wifi. Yes, some preparations need to be done so that it works.
vol=´adb connect 192.168.10.23:5555 2>&1 > /dev/null; adb shell dumpsys battery | grep level | cut -c 9-12; adb disconnect >/dev/null´; pactl set-sink-volume bluez_sink.0C_A6_94_AA_77_5D.a2dp_sink $vol%
(Inspired by: https://nitter.net/0xDesigner/status/1642554817590566915#m)
Reliably Getting #Bluetooth Working after Boot (Skript for #opensuse #tumbleweed)
As I described on the opensuse mailing list and in this mastodon thread, this is what happens after boot on my system (bluetooth USB dongle in Dell dock on an Acer laptop connected via USB-C, similar happens on Ryzen media stations).
This command line shows what happens, script is shown below
mfeilner@maldacena:~> BT-restart
Changing power on succeeded
Attempting to connect to 0C:A6:94:D1:77:5D
Failed to connect: org.bluez.Error.InProgress br-connection-busy
mfeilner@maldacena:~> BT-restart
Changing power on succeeded
Attempting to connect to 0C:A6:94:D1:77:5D
Failed to connect: org.bluez.Error.InProgress br-connection-busy
mfeilner@maldacena:~> BT-restart
Changing power on succeeded
Attempting to connect to 0C:A6:94:D1:77:5D
Failed to connect: org.bluez.Error.Failed br-connection-unknown
mfeilner@maldacena:~> BT-restart
Changing power on succeeded
Attempting to connect to 0C:A6:94:D1:77:5D
Failed to connect: org.bluez.Error.InProgress br-connection-busy
mfeilner@maldacena:~> bluetoothctl info
Device 0C:A6:94:D1:77:5D (public)
Name: PhilipsBT
Alias: Büro Regensburg
Class: 0x00240404
Icon: audio-headset
Paired: yes
Bonded: yes
Trusted: yes
Blocked: no
Connected: yes
LegacyPairing: no
UUID: Audio Sink (0000110b-0000-1000-8000-00805f9b34fb)
UUID: Advanced Audio Distribu.. (0000110d-0000-1000-8000-00805f9b34fb)
mfeilner@maldacena:~> cat bin/BT-restart
#!/bin/bash
sudo rfkill unblock bluetooth
sudo service bluetooth restart
sleep 3s
bluetoothctl power on
bluetoothctl connect 0C:A6:94:D1:77:5D
#Some other helpful commands I don’t need (anymore)
#sudo modprobe -r btusb; sudo modprobe -r btintel; sudo modprobe btusb; sudo modprobe btintel
#pactl set-default-sink bluez_sink.0C_A6_94_D1_77_5D.a2dp_sink
# /t.b.c.
mfeilner@maldacena:~>
#bipbip the #lucaapp remix loop (12” version 10:00)
#bip, #bipbip, #bipbipbip, #loop. Mit ffmpeg rumspielen, schabernack. Aber gerade die 10-Minuten-Dauerbeschallung ist so realitätsnah, irgendwie. #zusammenrottung.
Hier die Videos, die Anleitung steht unten:
BIP:
BIPBIP:
BIPBIPBIP:
BIPLOOP:
Bash HOWTO:
Die Schöpfungshöhe ist ja fragwürdig, bei dem hier, weil das unter #Linux so einfach geht. Erstmal habe ich den mit meinen GEZ-Geldern finanzierten, von den steuerfinanzierten Luca-App-Machern auf Youtube veröffentlichten Quelltext heruntergeladen. Ja, da ist noch ein wenig Overhead in Form von Bildern dabei, aber die entfernen wir später:
mfeilner@:~> youtube-dl “ytsearch:Smudo Luca Maischberger Woche”
[download] Downloading playlist: Smudo Luca Maischberger Woche
[youtube:search] query “Smudo Luca Maischberger Woche”: Downloading page 1
[youtube:search] playlist Smudo Luca Maischberger Woche: Downloading 1 videos
[download] Downloading video 1 of 1
[youtube] r66-5cDbNAE: Downloading webpage
[youtube] r66-5cDbNAE: Downloading MPD manifest
WARNING: Requested formats are incompatible for merge and will be merged into mkv.
[download] Smudo über Luca bei Maischberger Die Woche am 25.11.2020-r66-5cDbNAE.mkv has already been downloaded and merged
[download] Finished downloading playlist: Smudo Luca Maischberger Woche
mfeilner@al-khwarizmi:~>
Ups, das hatte ich ja schon runtergeladen. 😉 Habt Ihr gesehen, wie die Lucas auch dort alle Kommentare ausgeschalten haben? Da waren wohl wütende Opfer Kunden dabei?
Ok, dann den richtigen Ausschnitt ausschneiden: 2:32 bis 2:33:
ffmpeg -i Smudo\ über\ Luca\ bei\ Maischberger\ Die\ Woche\ am\ 25.11.2020-r66-5cDbNAE.mkv -ss 00:02:32 -to 00:02:33 -c copy bib-raw.mp4
Und im zweiten Nachgang genauer zuschneiden:
ffmpeg -i bip-raw.mp4 -ss 0.2 -to 0.4 -c copy bip.mp4
Aber so ein alleinestehender “Bip” ist doch langweilig, machen wir doch einen #bipbip, einen #bipbipbip und eine 10-Minuten-Loop daraus.
cp bip.mp4 bip1.mp4; ls bip*mp4 > files.txt; ffmpeg -f concat -safe 0 -i files.txt -movflags faststart -c copy bipbip.mp4
cp bip.mp4 bip2.mp4; ls bip*mp4 > files.txt; ffmpeg -f concat -safe 0 -i files.txt -movflags faststart -c copy bipbipbip.mp4
Und dann machen wir mal 10 Minuten bipbip mit Fade-In und Fade-Out:
fmpeg -stream_loop 1485 -f concat -safe 0 -i fileList.txt -movflags faststart -c copy loop1.mp4
ffmpeg -i loop1.mp4 -af afade=t=in:st=0:d=5,afade=t=out:st=590:d=10 loop.mp4
Und jetzt? Das hält doch keiner aus. Genau wie bei der #lucaapp.
Disclaimer: Dies ist Lernmaterial aus einem ffmpeg / Linux-Kommandozeilen-Kurs.
Linux – Bash Resize, split, Rotate or concatenate PDFs
This has probably been done a thousand times and ways, and much better than my humble fiddling. Consider this my memory pad for later.
I am doing some scripted pdf magic with files that come in from the scanner. They are either too big for web use, wrong format, not the right orientation (user error) or similar. So here’s a little collection:
Convert all (huge) PDFs into small ones with ghostscript (assuming ./Z-OLD for old versions exists):
for i in *.pdf; do gs -sDEVICE=pdfwrite -dCompatibilityLevel=1.4 -dPDFSETTINGS=/ebook -dNOPAUSE -dQUIET -dBATCH -sOutputFile=$i-small.pdf $i; mv $i Z-OLD/; rename .pdf-small.pdf .pdf *-small.pdf; done
Convert all PNGs in working directory into small PDFs (assuming ./png exists):
for i in *.png; do convert $i $i.pdf; mv $i png/; gs -sDEVICE=pdfwrite -dCompatibilityLevel=1.4 -dPDFSETTINGS=/ebook -dNOPAUSE -dQUIET -dBATCH -sOutputFile=$i-small.pdf $i.pdf; rename .png-small.pdf .pdf *.png-small.pdf; rm *.png.pdf; done
Concatenate PDFs into one file (the last argument is the new outputfile):
pdfunite A.pdf B.pdf C.pdf ABC.pdf
A lazy “rotate all” script that helps me if I put the paper on the scanner the wrong way. Leaves four versions of every pdf it finds, but 90/180/270° degrees tilted to the original.
#!/bin/bash
And yes, I know, there’s better ways. Worx 4 me, I guess. 🙂
INFILE=ls.txt
ls *pdf -1 > $INFILE
while IFS=”²” read -r line
do
PDF=`basename $line | rev | cut -c 5- | rev`
#left turn
pdftk “$line” cat 1-endwest output “$PDF”_left.pdf
#right turn
pdftk “$line” cat 1-endeast output “$PDF”_right.pdf
#turn 180 degrees:
pdftk “$line” cat 1-endsouth output “$PDF”_upsidedown.pdf
done <$INFILE
NetworkManager and Wol (WakeOnLAN)
That one little moment when the last of the systems that had failed for years to wake up on LAN finally gives up and does the job. I literally have no idea what went wrong on this little media station in the past, but a fresh install of Opensuse Tumbleweed fixed it. We’ve been looking into the BIOS so many times, systematically, comparing with its twin sibling, didn’t find a mistake. And also the NetworkManager dispatcher script was installed. I gave up and did a fresh Linux install. All I had to do then was adding this script:
#!/bin/bash
# /etc/NetworkManager/dispatcher.d/wol
#
#
# wol dispatcher script for NetworkManager
#
#
IFNAME=enp2s0
if [ “$2“ = “up” -a “$1“ = “$IFNAME“ ]; then
sleep 2
/usr/sbin/ethtool -s $IFNAME wol g
fi
… and make it executable (chmod a+x), done. Oh, make sure that the line starting with “IFNAME” (line 8) contains YOUR device’s name, not the random generated by your distributor and that the script really ends up in /etc/NetworkManager/dispatcher.d/wol.
Now my little upgrade script (don’t do this on production machines!) wakes up and updates the media station every morning while we are sleeping (all relevant data changed):
#!/bin/bash
# /usr/sbin/wakeup-update-mediastation
#
# Wakeup and update MediaStation
wol a8:a1:23:3e:g7:39
sleep60
ssh 192.168.0.222 ‘sudo zypper ref && sudo zypper dup -y -l –allow-vendor-change‘
sleep20
ssh 192.168.0.222 ‘sudo sync; sudo poweroff‘
logger “Mediastation successfully updated“
It’s invoked by the cron job:
0 6 * * * /usr/sbin/wakeup-update-mediastation
Your mileage may vary when it comes to user priviledges (sudo or ssh as root, make sure you do the right thing!)
Unlimited Screen Estate and machines at your mouse/kb, w/o KVMs, all in #opensource: #barrier
Barrier: A Free, Open-Source and Cross-Platform Alternative to Synergy
“You’ve probably heard of Synergy before. If you didn’t, Synergy is a piece of software that allows you to shares one mouse and one keyboard between multiple computers. A great piece of software that costs $29 for the basic version and $39 for the pro version. If you’d love to have the capabilities that Synergy provides but don’t want to fork over $29, you should check out Barrier which is free, open-source and cross-platform. Synergy started as an open source project. So the guys over at Barrier forked that original Synergy project, updated it and kept it’s minimalistic design.”
(Housekeeping) #Backup Script for #Nextcloud
I don’t know if others need that too, but it seems just naturally to post this tiny little piece of bash which is our Nextcloud backup script. And I am perfectly aware that this is SME style, not big iron. 🙂 And if you don’t like Databases or PHP, have a look at Owncloud Infinite Scale.
These two products have been targeting more and more diverging directions since their fork: Owncloud adresses large scale, scalable datacenter customers (like CERN) and promises 10 times faster speed than their own PHP solution, but Nextcloud is carving out market share from MS365 customers with gazillions of apps in their app store and a large PHP community – with all benefits and downsides. Raise your hand if you never had to deactivate some community app to make an update work! 🙂
MySQL-Root-Password
Important: your MariaDB-Passwort will be in this file, I didn’t spend much time into investigating workarounds, but a chmod 700 of this file (read-write-execute) for root only seems appropriate. The DB is not listening on anything else but localhost, thus I am ready to accept this. If there’s a simple solution I missed, answer on Twitter or drop me a PM/Mail/Matrix message.
The Backup Script
As you can see I am backing up to a separate volume. I have file servers in several locations that fetch their backups (the tar files) from there. I don’t want the root fs run full, thus I don’t do a backup if /backup is not mounted. Alerting is done elsewhere. 🙂 On other systems, I mount the backup drive during such a script’s run. If you’re (like me) a seasoned but unexperienced Bash starter, add some “sleep 30” between the lines to see what’s happening and to easily break the script’s run. And you may or may not want the option –delete for rsync – your mileage may vary – and sorry for wordpress changing dashes and hyphens (Remember “Non-hyphenated is an example of a hyphenated word”).
#!/bin/bash
# Backing up Nextcloud Server
# Database Root password is in here, so chmod 700 this file!
DIR=/var/www/nextcloud #Source
BACKUPDIR=/backup/nextcloud #Target
BACKUPTAR=/backup/current_nextcloud_backup.tar.gz
DBPASS=YOUR_PASSWORD_HERE
if grep -qs ‘/backup ‘ /proc/mounts; then
echo“Backup disk is mounted. Proceeding with backup from $DIR/.“
echo“Entering nextcloud directory“
cd /var/www/nextcloud
echo“Putting NC into maintenance mode“
sudo -u www-data php occ maintenance:mode –on
echo“Backing up folders and config with Rsync:“
# sleep 30
/usr/bin/nice -18 /usr/bin/rsync -Aavz –delete $DIR/ $BACKUPDIR/
echo“Backing up MySQL data base ‘nextcloud’ :“
mysqldump –single-transaction -h localhost -u root -p$DBPASS nextcloud > $BACKUPDIR/nextcloud-sqlbkp_`date +“%Y%m%d“`.bak
sudo -u www-data php occ maintenance:mode –off
/usr/bin/nice -18 /bin/tar -czf $BACKUPTAR $BACKUPDIR
else
echo“Sorry, Backup disk is not mounted, quitting. CU again tomorrow.“
fi
Update:
I have two aliases on my NC servers:
alias ncd=’cd /var/www/nextcloud’
alias occf=’sudo -u www-data php ./occ’
With these I don’t need to bother about different document root directories (Debian/Ubuntu/Suse) nor remember the sudo… syntax (yes, I’m old) :-).
That proves helpful to do a lot of occ commands, like cleaning up the hard way:
occf trashbin:cleanup –all-users
occf versions:cleanup –all-users
clean up all trashbins and remove all old versions of files (yes ALL!).
If you don’t want Nextcloud to slowly fill up your hard drive / storage, add this to the config.php file:
‘trashbin_retention_obligation’ => ‘auto’,
‘versions_retention_obligation’ => 60, ‘auto’,
These two options will make Nextcloud store only files that are younger than 30 in the trashbin and versions of files no longer than 60 days.
#openSUSE in #RaspberryPi – Quickstart Guide
#Leaflet … notice to self… study.
Leaflet – a JavaScript library for interactive maps
Leaflet is the leading open-source JavaScript library for mobile-friendly interactive maps. Weighing just about 39 KB of JS, it has all the mapping features most developers ever need. Leaflet is designed with simplicity, performance and usability in mind. It works efficiently across all major desktop and mobile platforms, can be extended with lots of plugins, has a beautiful, easy to use and well-documented API and a simple, readable source code that is a joy to contribute to.
PGP/S-MIME on Linux Command Line, helping Kontact (and other Mailers)
I recently had to decrypt a PGP/S-MIME encrypted mail. It’s been a long time since I was confronted with that format, and KDE’s Kontact does not seem to support this out of the box– actually only Thunderbird seems to do, and that’s not on my machines. Here’s what I did.
This Mail came in.
With the right PGP-Key I could decrypt it:
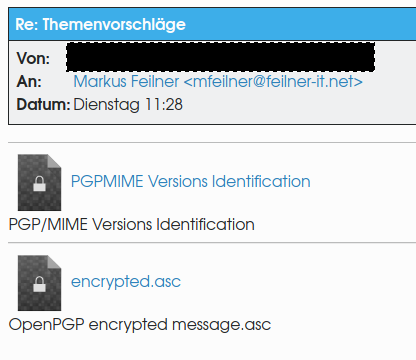
Upsii… there’s another encrypted file in there, exactly as the standard RFC from 2001 defines – this way even attachments are hidden from those that don’t have the private PGP key.
Since KDE’s crypto engine couldn’t help, and Thunderbird is not configured on my machines, I went to the command line. I saved the attachment “encrypted.asc” and ran the command “gpg –output uncrypted.asc –decrypt encrypted.asc“:
mfeilner@alquarismi:~/Downloads> gpg –output uncrypted.asc –decrypt encrypted.asc
gpg: WARNUNG: Unsichere Zugriffsrechte des Home-Verzeichnis `/home/mfeilner/.gnupg’
gpg: verschlüsselt mit 4096-Bit RSA Schlüssel, ID XXXXXXXXXXXXXXXXX, erzeugt 2015-04-24
(…)
gpg: verschlüsselt mit 2048-Bit RSA Schlüssel, ID XXXXXXXXXXXXXXXXX, erzeugt 2018-12-25
(…)
mfeilner@alquarismi:~/Downloads>
… and that way I got a file named uncrypted.asc that I could open with my favorite text editor or emacs.
#OSS rocks. #Linux Rocks. Autorotate PDFs
#Linux has some mighty PDF Toolkits. One of them is pdftk. I am using it so that we don’t have to bother anymore about orientation of Files on the scanner. We just delete the wrong ones. 🙂
!/bin/bash
(use the right upticks ` in the basename line, wordpress messes them up…)
INFILE=ls.txt
ls *pdf -1 > $INFILE
while IFS=”²” read -r line
do
PDF='basename $line | rev | cut -c 5- | rev‘
#Links drehen:
pdftk “$line” cat 1-endwest output “$PDF”_left.pdf
#Rechts drehen:
pdftk “$line” cat 1-endeast output “$PDF”_right
#180 degrees:
pdftk “$line” cat 1-endsouth output “$PDF”_upsidedown.pdf
done <$INFILE
Linux Malware, Woodcutters and James Bond stories.
FBI Reports On Linux Drovorub Malware | Hackaday
This is a modern spy story, but not quite what we’ve come to expect in Bond movies. “Well, Moneypenny, it appears Spectre is using the POCO library to generate UUIDs,” is hard to work into a trailer. We prefer the old days when high-tech spying meant nonlinear junction detectors, hacking Selectrics, moon probe heists, and passive bugging.
Pihole explained. Hehehe. Werbefrei surfen auch mit dem iPhone.
Sicher und werbefrei surfen mit dem Raspberry Pi
Diese Hardware brauchst du für den Raspberry Pi mit Pihole:
Einen Raspberry Pi – im Grunde tut es jeder Raspberry, auch der Raspberry Pi 1 oder Zero. Wir empfehlen euch jedoch einen Raspberry Pi 3 und aufwärts, um die Weboberfläche vom Pihole flott nutzen zu können.
Ein Netzteil – oder einen USB-Anschluss mit 2A-Output oder mehr.
Eine Micro-SD-Karte und einen SD-Adapter, der Karten meistens beiliegt.
Optional: Ein Gehäuse für den Raspberry Pi.
Optional: Einen Hoodie, da ihr ein paar einfache Shell-Befehle kopieren werdet und dabei aussehen müsst, wie ein Hacker.
Mount all USB-Disks in one go (Linux, Bash, One line)
for i in `ls -1 /dev/disk/by-uuid/`; do mkdir /mnt/$i; mount /dev/disk/by-uuid/$i /mnt/$i; done
Yes, I am not a big expert, and I know this can be done shorter, I assume… something like “for i in /dev/disk/*” or so, I assume. Works for me, though.
My linux journal took too many GIGs of HD space…
Managing Journal Size – The Ultimate Guide To Logging
Deleting or Vacuuming Journals To delete archived journal entries manually, you can use either the –vacuum-size or the –vacuum-time option. In the example below, we are deleting any archived journal files, so the journal size comes back to 200MB. $ journalctl –vacuum-size=200M
@debian @debconf #Minidebconf 2020 in Regensburg
APELL is an association of the national Open Source Business Associations @osballiance
APELL is an association of the national Open Source Business Associations @osballiance, @cnll_fr and @cossfi. @OpenForumEurope will be Advisory Member. We will soon release detailed information and how you can join and collaborate, stay tuned!
— OpenForum Europe (@OpenForumEurope) January 31, 2020
Google open-sources the tools needed to make 2FA security keys | Engadget
https://www.engadget.com/amp/2020/01/31/google-open-sources-the-tools-needed-to-make-2fa-security-keys/
