Reality update: Normalization of Deviance – Flight Safety Foundation … :
“Noncompliance with standard operating procedures (SOPs) — especially tolerance of unstabilized approaches — is a serious impediment to further reduction of accident risk, according to United Airlines safety leaders.
During his April presentation to the World Aviation Training Conference and Tradeshow (WATS 2015) in Orlando, Florida, U.S., Chris Sharber, a first officer and flight simulator instructor–Boeing 777 fleet, at the United Airlines Training Center in Denver, described the issue as invisible and insidious.
United Airlines safety leaders echoed this theme in a keynote address and in presentations about analytical techniques and related insights from the company’s safety management system (SMS), including analysis of flight crews’ voluntary safety reports.
“We have somewhere between 11,000 and 12,000 pilots. Our new-hire department will bring another 1,000 pilots on board in the next 12 to 15 months,” Sharber said. “One of the challenges that you face with that many pilots, of course, is SOP compliance. How do you influence a group of 11,000 individuals to focus on SOP compliance, to maintain the tight standardization that’s required to maintain safe operations in a global airline?””
(…)
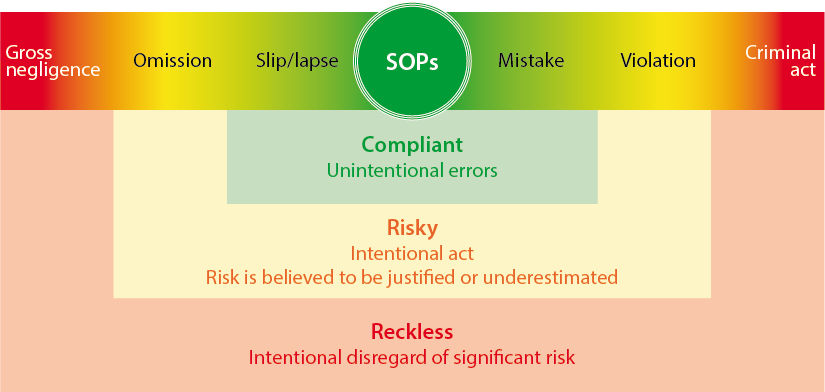
“Intentional Noncompliance Flight crews engage in intentional noncompliance — and sometimes self-justify this behavior — out of a variety of motivations. “Maybe it’s a bad SOP. Maybe there are competing priorities. Maybe it just doesn’t work. It’s not functional. … It’s not that important. It doesn’t really matter. I might [take a] shortcut just because I’m trying to save time,” he said. “[Or pilots rationalize], ‘I just don’t like it. I like the way we did it before. I’ve got a better way of doing things. I think this is a bad idea. I’m just not going to do it.” These occur with a perceived lack of consequences. The LOSA Collaborative’s latest data analysis suggests that acts of intentional noncompliance occur on between 40 to 60 percent of flights, or about half, on average.”
Reality update: Normalization of Deviance – Flight Safety Foundation … :
 “
“
 “
“


 Reality update:
Reality update: