Tag: data security
Facebook wants to reveal your name to the weirdo standing next to you – Naked Security
Why do we get such stupid ads? Because it’s only a numbers’ game…
 Newco Shift : Dear Advertising Industry: Please Do Better. You’re Killing the Open Web. … :
Newco Shift : Dear Advertising Industry: Please Do Better. You’re Killing the Open Web. … :
“Let’s apply that reality to our robe example. Let’s say the robe costs $60, and yields a $20 profit for our e-commerce advertiser, not including marketing costs. That means that same advertiser is can spend upwards of $19.99 per unit on advertising (more, if a robe purchaser turns out to be a “big basket” e-commerce spender). So what does our advertiser do? Well, they set a retargeting campaign aimed anyone who ever visited our erstwhile robe’s page. With CPMs averaging around a buck, that robe’s going to follow nearly 20,000 folks around the internet, hoping that just one of them converts.“
What is an “Exploit” – German article explains
Have an hacker explain why an “exploit” is like an access or an unwanted access permission to your system. Nice read, albeit German.
https://www.golem.de/news/hacker-was-ist-eigentlich-ein-exploit-1806-134909.html
The City of Atlanta, Georgia has been hacked.
 Reality update: Hackers Are Holding The City of Atlanta Hostage … :
Reality update: Hackers Are Holding The City of Atlanta Hostage … :
““This is much bigger than a ransomware attack, this really is an attack on our government,” Atlanta Mayor Keisha Lance Bottoms said at a news conference, Reuters reports. “We are dealing with a (cyber) hostage situation.”
(…)
Experts have warned that cybersecurity is likely the next great security threat for governments and companies around the world, and that most systems are simply not prepared. Indeed, Atlanta isn’t the first U.S city to be hit by ransomware — the Colorado Department of Transportation has already been hit twice in 2018. However, the Atlanta attack seems to the most thorough, city-wide cybersecurity breach yet. And though some companies have ramped up security following attacks, as Atlanta plans to do, it seems that most cities aren’t adapting their security before an attack happens.
(…)
It’s not yet clear at what point Atlanta will give in and pay the ransom to get its data back. But as more cities rely on digital processes, the dangers to both citizen privacy and security are going to multiply. Imagine a hack that takes out not just a city’s computer systems, but also its electrical power, plumbing, and even control of your own car.“
Microsoft is now censoring its users, scanning all content for “inappropriate” stuff
 Reality update: Microsoft to ban ‘offensive language’ from Skype, Xbox, Office | CSO Online … I doubt this is fine with German data protection laws:
Reality update: Microsoft to ban ‘offensive language’ from Skype, Xbox, Office | CSO Online … I doubt this is fine with German data protection laws:
“Better watch out if you are playing Xbox, get ticked, and cuss. Microsoft might ban you for the “offensive language.” If they do, then say bye-bye to your Xbox Gold Membership and any Microsoft account balances.“
Darknet demystified – The Limits of Anonymity.
The error is on OSI Layer 8, and even the best technology won’t help you if you use it wrong. In this article about the Darknet (Heise I’X, in German) I demystify many “given” assumptions. No NSA, no police, nobody needs to crack your cryptography if you do the same silly mistakes like so many others before you.
Update: Early in February I was interviewed by Radio Berlin Brandenburg about the my opinion on the darknet.
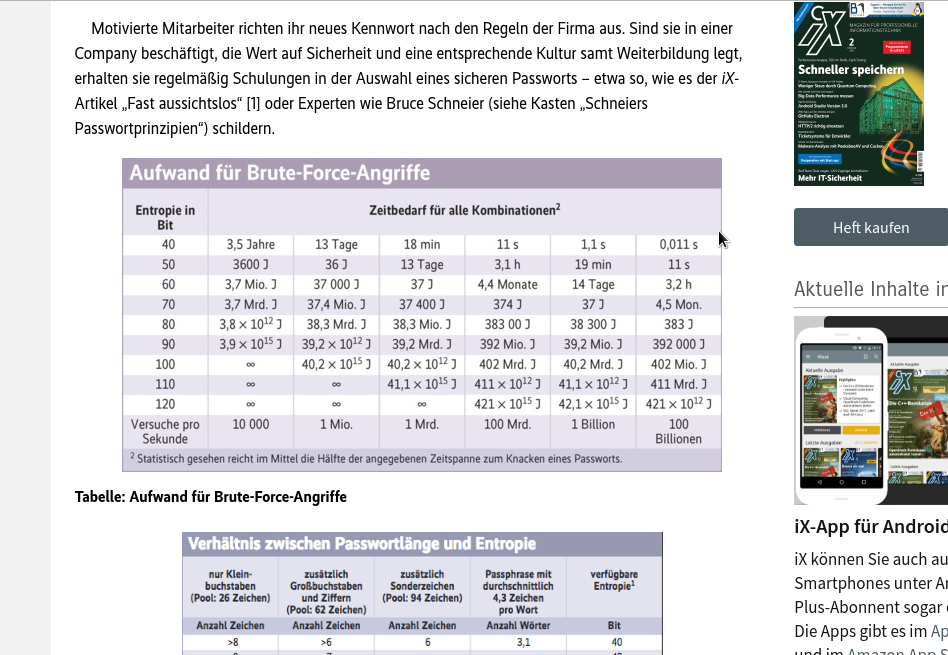
Wechselwahn – why it does not make sense to enforce recurrent password changes.
In this article for Heise I’X (in German) I present statistical and empirical evidence why it usually is a bad idea to force your users to change their password regularly. In fact, you’ll maybe push users to use patterns for their passwords that are cracked much easier than their password. What is a good password, and why you should only change it when you have reason for doubt. “You will need good reason to push your users into regularly changing their passwords – and only in few cases or insecure environments this may make sense at all…”
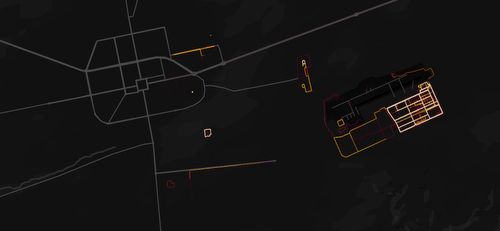
Army people love to be fit – and their devices show it… on maps
How to find secret army bases via health trackers… (German article)
Soldiers using their fitness trackers tell the world where their army bases are located. #sigh.
Feeling safe? That’s all that matters. A blog.

Security Theater. When feeling and reality don’t match it will become very likely that someone shows up to either sell some of his magic snake oil to you or try to convince you to that you need new laws or rules. #Sigh.
ePrivacy – Keynote at 34th Chaos Communication Congress
At the 34th CCC meeting – the legendary Chaos Communication Congress – Ingo Dachwitz held an interesting speech about a highly controversial topic: We all want our data to be safe. But what is really necessary for a well informed understanding of data security of individual users? Can we declutter ePrivacy?
Watch here: https://netzpolitik.org/2018/34c3-eprivacy-macht-der-datenschutz-das-internet-kaputt/
#Meltdown-#Spectre: I Guess the NSA knew about it since 1995…
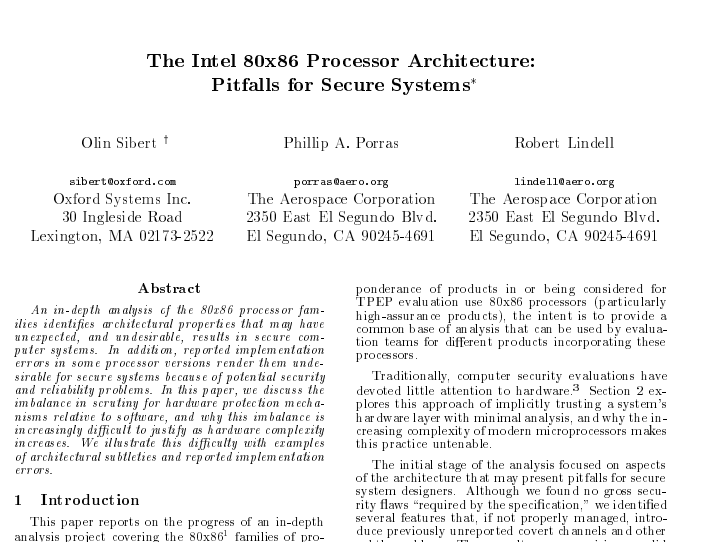 Here is a study from 1995 which was paid for by the NSA (I guess that is what “under the auspices” means?) and that comes to very frightening findings. Well, at least if you’re in security and IT:
Here is a study from 1995 which was paid for by the NSA (I guess that is what “under the auspices” means?) and that comes to very frightening findings. Well, at least if you’re in security and IT:
“An in-depth analysis of the 80×86 processor families identifes architectural properties that may have unexpected, and undesirable, results in secure com-
puter systems. In addition, reported implementation errors in some processor versions render them undesirable for secure systems because of potential security and reliability problems.”
“This analysis is being performed under the auspices of the National Security Agency’s Trusted Product Evaluation Program (TPEP).”
I think this study sheds a strange light on the following quote from the Washington post:
“Rob Joyce, White House cybersecurity coordinator, said, “NSA did not know about the flaw, has not exploited it and certainly the U.S. government would
never put a major company like Intel in a position of risk like this to try to hold open a vulnerability.”