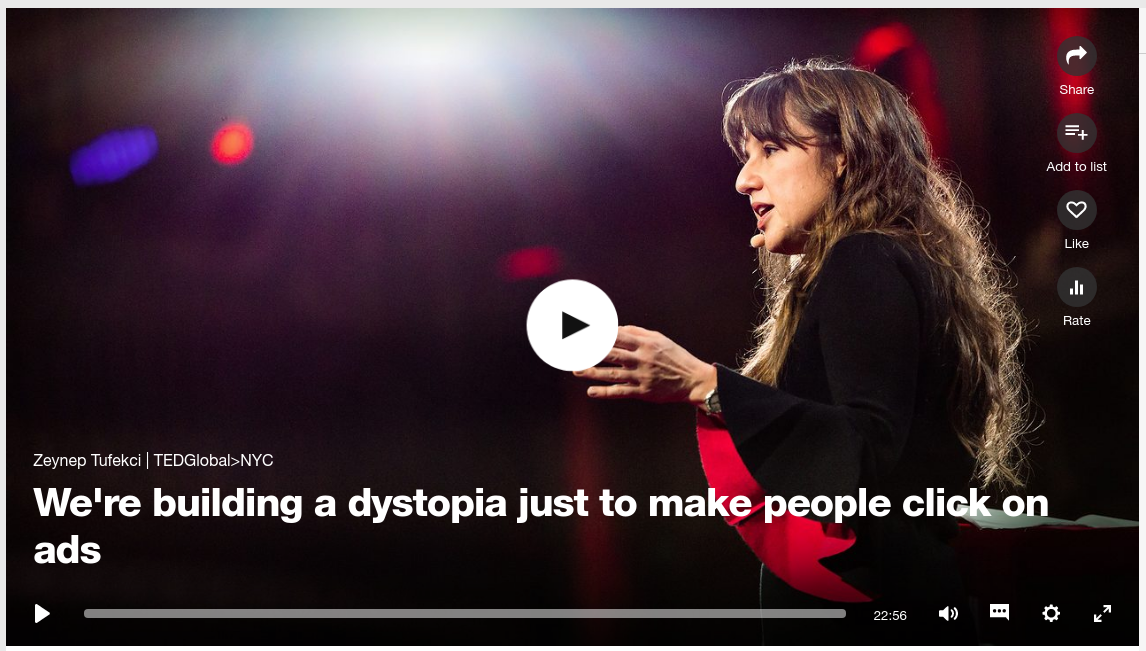
It’s been already six years that I wrote the Linux-Magazin article about hacking Android for banking data “Googles Smartphone-Linux ist ein einfaches Opfer für Angreifer“, and even a little more since me and Gunnar Porada met at Cortal Consors Bank. He was presenting, I was invited as a journalist.
It’s been already six years that I wrote the Linux-Magazin article about hacking Android for banking data “Googles Smartphone-Linux ist ein einfaches Opfer für Angreifer“, and even a little more since me and Gunnar Porada met at Cortal Consors Bank. He was presenting, I was invited as a journalist.
And the weird thing was: Cortal Consors, a big bank that in the past had specialized on trading stocks and stuff, had invited Gunnar to show us why SMS-TAN (Mobile TAN) and similar smartphone-based “Two-Factor-Auth” mechanisms are merely security theater, like every trick that includes the smartphone. Nevertheless, they said, they’d still recommend to use it, since “it is not actively being hacked”. Well, that has changed for sure in the last years. 🙁
Albeit this article is merely available in German, it’s a good read – have Google translate it. The following quote says basically that it’s less effort to hack both Windows PC and Android device (since they will be in the same Wifi sometime) than it takes to find out two devices belong together. I just realized that again, I had written about some topic that didn’t have a name then: CDT (Cross Device Tracking).
If you feel fine with Security by Obscurity, then SMS-TAN or Photo-TAN or Face recognition might be enough for you. It’s not for me.
“„Technisch ist das gar nicht so aufregend, die Angriffsmöglichkeiten sind bekannt. Das Schwierigste für den Angreifer ist eher herauszufinden, welches Handy zu einem infizierten PC gehört“, erklärt der Ex-Hacker, der gerade 100 000 Euro vom Konto eines Konzerns zu einer gemeinnützigen Organisation transferiert hat, mit gefälschten Accounts und Webseiten, auf die er den Demo-Rechner vorher per DNS-Spoofing umgeleitet hat – natürlich nur als Demo fürs Publikum.“
 “According to a recent paper, published on March 12 in the journal Physical Review D, the final moment for the universe will be triggered by a bizarre consequence of subatomic physics called an instanton.
“According to a recent paper, published on March 12 in the journal Physical Review D, the final moment for the universe will be triggered by a bizarre consequence of subatomic physics called an instanton. You may have been thinking that the good old beep tool is safe, but you’re wrong …
You may have been thinking that the good old beep tool is safe, but you’re wrong …



 … For years I have been talking about the dangers of QR codes…. well here’s one of the convenient Apple preload functions, I assume, messing it up:
… For years I have been talking about the dangers of QR codes…. well here’s one of the convenient Apple preload functions, I assume, messing it up: